IT infrastructure of a contemporary company is a complex mechanism that includes а multitude of corporate systems: network monitors, antiviruses, applications, databases, operating systems of servers and PCs, Active Directory, Exchange. Technically, any event in the system gets logged (protocoled). But it is impossible to track, analyze, and react timely to all events without an automated system.
SIEM can gather information almost from every source:
- Event logs of servers and workstations
Used to control access, compliance with information security policies
- Access control, authentication
Information system access rights control
- Antiviruses
Information about availability, reliability, and validity of antivirus SW, information about infections, virus epidemics, and malware
- Virtualization environments
Virtual machines creation, usage, and deletion control
SearchInform SIEM Reveals
- Virus epidemics and separate infections
- Attempts to gain unauthorized access to data
- Account password guessing
- Active accounts of dismissed employees that had to be deleted
- Hardware configuration errors
- Permissible operating temperature abuse
- Data removal from critical resources
- Use of corporate resources during off-duty time
- Virtual machines and snapshots removal
- Connecting new equipment to IT infrastructure
- Group policy changes
- TeamViewer usage, remote access to corporate resources
- Critical events in protection systems
- Errors and failures in information systems
Software Objectives
The sheer number of event sources nowadays is so high that it’s impossible to manually control all events in the infrastructure. And this might lead to the following risks:
- Overlooking of a security violation
- Failure to identify details and determine causes (due to event log clearance, etc.)
- Lack of instruments for event reconstruction
And SearchInform SIEM, as an aggregator of information from different devices, solves this problem. The system unifies the data and provides a secure storage for the data.
SearchInform SIEM does not just correlate events, but also evaluates their significance: the system visualizes the information focusing on important and critical events.
A single event is not always indicative of an incident. For example, a single failed logon might be just accidental, however, three or more attempts probably indicate a password-guessing attack. To identify really critical events, SearchInform SIEM uses rules that contain a whole range of conditions and take into account the most diverse scenarios.
Automated notifications and incident management enable SearchInform SIEM to fulfill its main purpose: Create conditions for information security officers to rapidly respond to incidents. The solution provides automatic detection of incidents.
Cases
Unauthorized access to corporate email
Administrator of a mail server can reconfigure the system to get access to email of a top manager or other employee. SIEM will promptly react to the incident and notify information security department.
Adding accounts: deactivation, change of name, and simple password
Employees who do not change passwords for a long time or give it to someone else are also at risk. Besides, an administrator can temporarily rename someone’s account and give network access to intruders. SIEM will inform you if it detects such incidents.
Correlation of unrelated data
There are situations when events, seemingly harmless, together can pose great threat. For example, when someone sends a password to a top manager’s account. This event will not attract attention but, if later this account accesses critical resources, the system will alert to the incident.
Detection of unusual violations
One savvy employee was trying to copy client base in an unusual manner. The employee’s account did not have rights to obtain data from CRM. The employee created a new DBMS account and tried to get information directly from the database. One of the SIEM policies managed the access of new accounts to the database, and the system immediately notified specialists about the violation.
Advantages
- Quick implementation without intensive preliminary configuration, the software can start working on the installation day
- Easy-to-use system, a specialist without IT skills will cope with the program as it doesn’t require knowledge of programming languages to create correlation rules
- Integration with SearchInform products increases the level of information security of a company and makes it possible to fully investigate the incident and collect evidence base
- Low hardware and software requirements and reasonable price even for small-sized business
Preset Security Policies
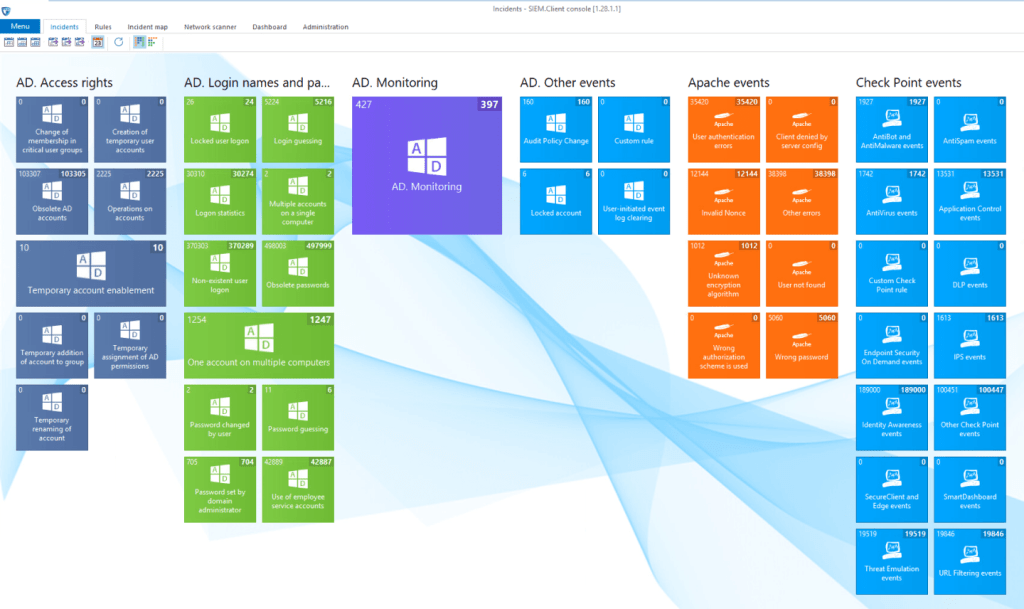
Upon the system installation, the information security staff gain access to 300+ ready-made rules – security policies. Users can edit and customize existing rules and create their own policies. Out-of-the-box security policies scan the following data sources:
- Operating systems
- Email servers
- Domain and workstation controllers
- Linux servers and workstations
- Antiviruses
- Firewalls and integrated network security devices
- Solutions on the 1C platform
- Other syslog sources
- Environments
- DBMS
- DLP systems
- File servers
- Virtualization
The sophisticated mechanism of SIEM operation boils down to the following algorithm:
- Collecting events from various sources (network hardware, PC, security systems, OS)
- Bringing heterogeneous data to a common denominator
- Analyzing data and detecting threats
- Pinpointing security breaches and sending alerts in real-time mode
SearchInform SIEM* collects information from various sources, analyses it, discovers threats, and alerts the designated info-security staff.
*For informational purposes only. Part of the described functionality of SearchInform SIEM is under revision. The project for the system capabilities expansion is being implemented in the format of co-financing based on the vendor’s own funds and the Russian fund of information technology development grant.
What Business Tasks Does SIEM Solve?
IT infrastructure of a today’s company is a complex mechanism that includes many corporate systems:
Firewall
Antiviruses
Applications
Databases
Virtualization environments
Network hardware and other hardware
Active Directory
OS servers and PCs
Every system is a source of personal, financial and corporate data that violators aim to obtain.
The company can be endangered both by actions of system administrators (unauthorized granting of access rights, creation or deletion of accounts, firewall disabling) and by vulnerability of the products through which violators can get access to a company’s data.
SIEM accumulates information from different sources, analyzes it, detects incidents, and notifies about them