SearchInform Risk Monitor
Provides your business with multifaceted protection against financial losses caused by internal threats in several stages:
The system operates on two levels. It keeps track of the data leaving the network while at the same time monitors employee activities on computers. SearchInform Risk Monitor keeps an eye on the company’s assets 24/7 even if the employees are located off the premises of an organization but using corporate devices.
SearchInform Risk Monitor Control
The system conducts a real-time analysis, identifying every ongoing event within a network and mitigating insider risk. The software saves the data it obtains and allows you to restore the details, enabling retrospective investigation and providing access to the archive.
SearchInform Risk Monitor Components

Objectives
SearchInform Risk Monitor aids your company in building a risk management program and a solid insider threat management process, helping you foresee any prospective internal corporate risks in advance via:
- Immunization to the consequences of data leakage
- Exposing fraud schemes (sabotage, embezzlement, theft, waste, kickbacks, and more)
- Safeguarding the company against personnel risks and predicting employee behavior patterns
- Solving regulatory compliance issues
- Helping to increase staff productivity
- Team loyalty management
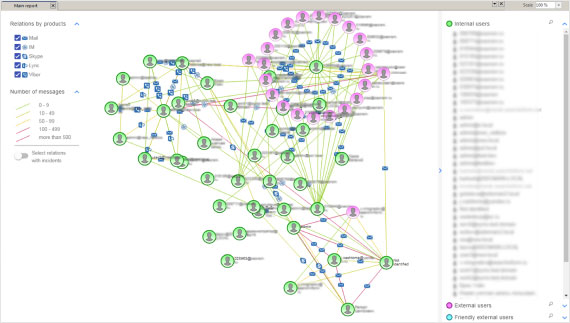
Reports
SearchInform Risk Monitor’s reports visualize all the activities taking place within a company. Having an objective and detailed idea of all processes and activities provides a means to stop violations and analyze possible threats for the purpose of preventing potential incidents.
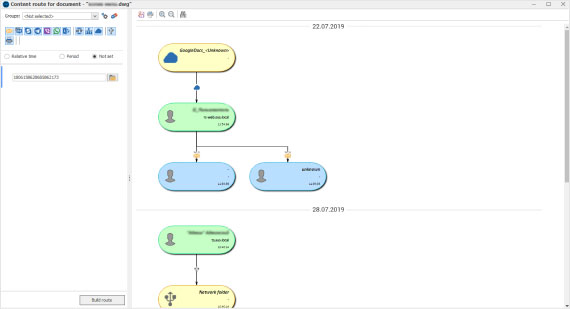
Cases
MailController
Records all email correspondence (Gmail, Yahoo, Hotmail, etc.)
CloudController
Controls files moved from/to cloud storages (Google Disk, Dropbox, etc.)
IMController
Records chats and captures attachments on social networks and instant messengers
FTPController
Captures data sent or received over FTP, including encrypted connection (FTPS)
DeviceController
Captures data transferred by users to external devices
AlertCenter
Manages setting security policies, allows you to edit preconfigured policies, create rules and schedule audits
PrintController
Monitors the content of documents sent for printing
ReportCenter
Visualizes user activities across all communication channels, all events within a system and connections between employees
HTTPController
Captures files and messages transmitted over HTTP/HTTPS protocols
Data at rest monitoring
UBA
Forensic Suit
Time Tracking
Performance Evaluation / Efficiency Monitoring
Analytical Capabilities
To protect your business and identify internal risks, you should be monitoring behavior within your team. Thanks to powerful text, audio, video, and graphics analysis along with an embedded UEBA component, SearchInform Risk Monitor renders corporate fraud predictable and financial losses preventable.
General-Purpose
Relevant for any company
Regardless of the business field, SearchInform helps monitor pay-offs and corruption, provides workplace morale analysis, detects risk groups, and more.
Industry-Specific
Tailored for particular industries.
Takes into account the company’s sphere of business: financial services, insurance, manufacturing, healthcare, retail, etc.
Customized
Solves specific tasks for a client.
The SearchInform experts develop security policies cost-free at the client’s request, which are necessary to comply with the corporate rules and local law.
SearchInform clients get to test the product and get a feel for its value to their businesses before they buy it. The trial features the products full set of functions and training.
SearchInform Risk Monitor is a multi-component system. All the solutions are smoothly integrated. Clients can purchase the full software packages or select among particular modules of the product and customize their own bundle.
And this can be done by the client’s staff. There is no need to disclose the internal documents and processes. Moreover, the SearchInform experts will provide round-the-clock technical support to the clients.
SearchInform clients get to test the product and get a feel for its value to their businesses before they buy it. The trial features the products full set of functions and training.
SearchInform Risk Monitor is a multi-component system. All the solutions are smoothly integrated. Clients can purchase the full software packages or select among particular modules of the product and customize their own bundle.
SearchInform teaches its clients how to operate the software, helps develop security policies, provides consulting on the interception analysis, and keeps clients updated on new software features and capabilities.
Technical Advantage
SearchInform Risk Monitor holds 4 key advantages over its competitors
SearchInform Risk Monitor allows you to monitor all critical communication channels. A complete list of both corporate (Exchange, Lync, etc.) and personal (WhatsApp, Skype, etc.) communication tools is supported. This allows the safe use of network channels without the need to block them.
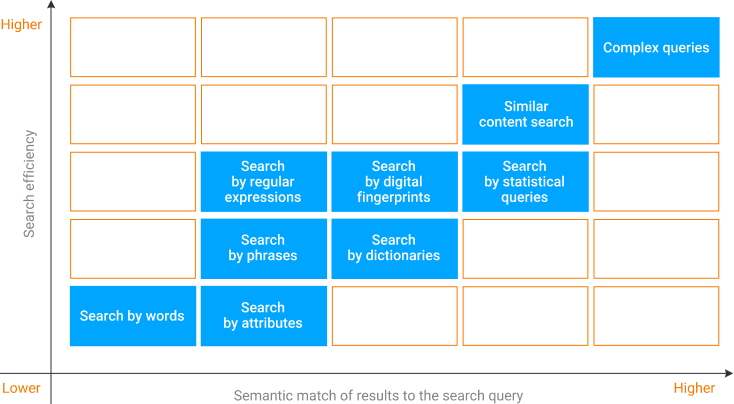
In addition to ordinary analysis technologies (stemming, dictionaries, regular expressions, digital fingerprints, OCR), SearchInform Risk Monitor utilizes a spectrum of unique technologies that help increase the system's efficiency. Detection of texts that are close in meaning to samples. Search for images similar to sample images. Search any audio or video recording users are involved in.
The product provides a basis for audio and video recordings of user activities, recording any activities involving files or folders, audit logs, devices, or software. Constant monitoring tools allow you to accurately reconstruct a chain of events and discover employees engaged in violations.
SearchInform Risk Monitor presents a built-in feature that allows you to evaluate user productivity in applications and on websites. This provides you a means to expand applicable scope of the system, increase the level of employee loyalty, and anticipate business issues ahead of time.