Managing Internal Track
SearchInform helps your company fulfill its risk management program, facilitate regulatory compliance and investigation processes, prevent corporate fraud, and detect employee abnormal behavior.
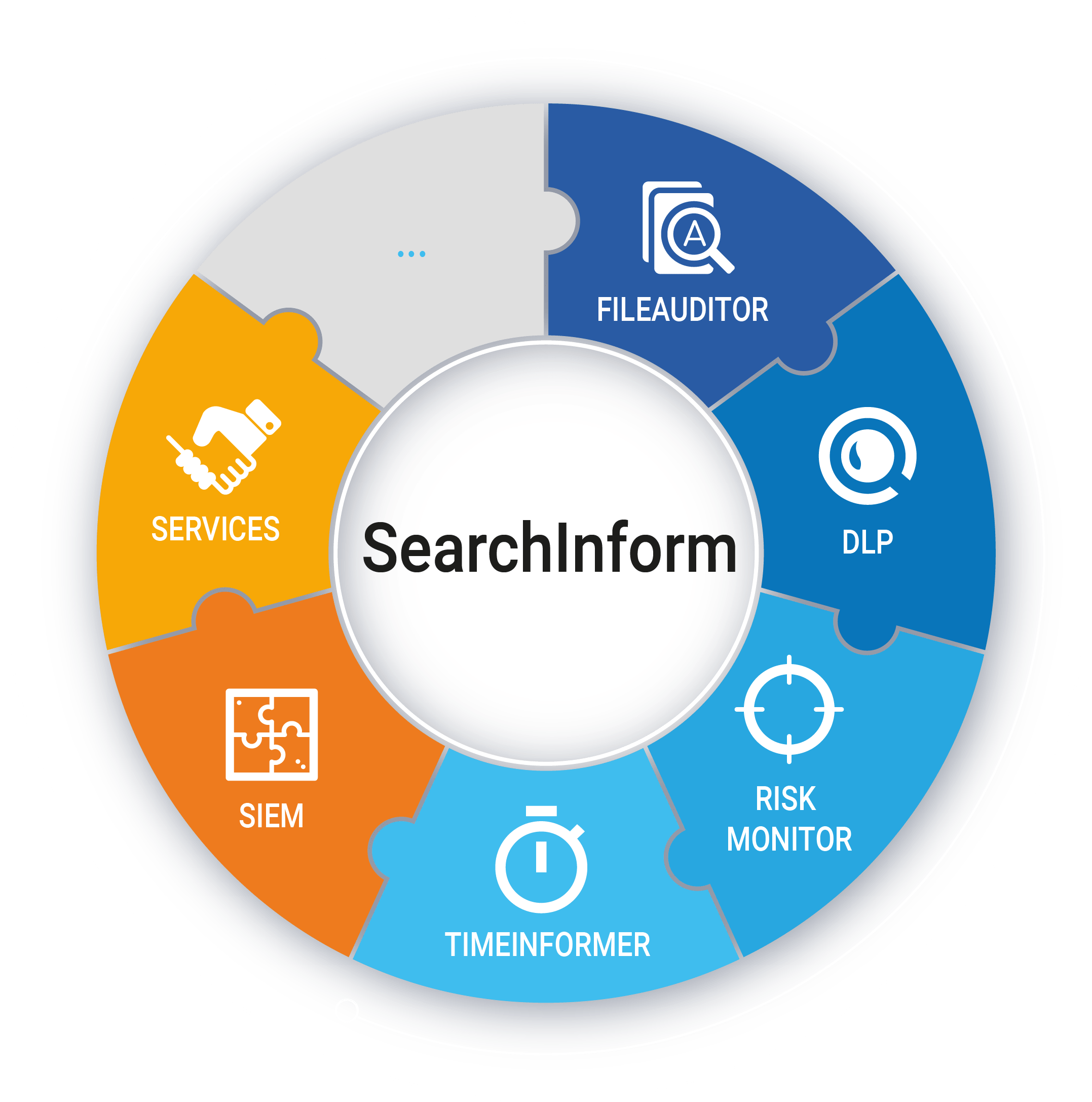
Challenges
All the tools and features you need to keep your company protected and solve the most complex monitoring issues.
